However, as Microsoft's Defender ATP Research team which spotted the attack says, "behavioral blocking and containment capabilities in Microsoft Defender ATP detected and foiled the attack in its early stages, protecting customers from damage."
Credential theft attack chain
To distribute the Lokibot payloads, the attackers used highly-targeted spear-phishing emails with contents specifically tailored to the targeted organization.
For instance, in the case of a pharmaceutical firm, they "used pharmaceutical industry jargon to improve the credibility of the email and in one case requested a quote on an ingredient that the target company was likely to produce."
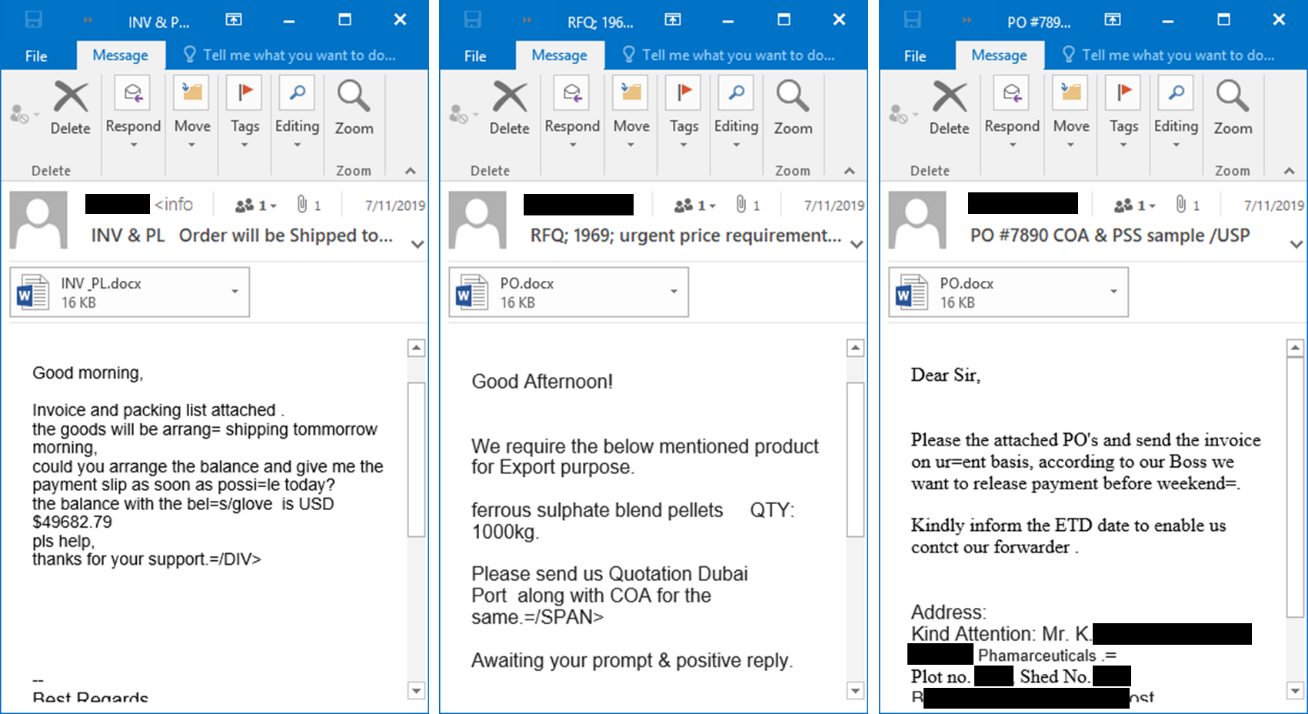
To compromise the victims' systems, the phishing email attachments would load malicious code from an attacker-controlled WordPress website when the targets would open the lure documents.
In the next step, the CVE-2017-11882 remote code execution vulnerability in the Microsoft Office Equation Editor component would be abused by the remotely loaded exploit code and, after successful exploitation, the Lokibot malware would be downloaded and dropped.
LokiBot collects as much sensitive info as possible, info that subsequently gets delivered to the malware operators' command and control (C2) servers via an HTTP POST request.
The LokiBot malware is known for stealing a wide range of credentials including but not limited to email account passwords, FTP credentials, browser-stored passwords, and more.
Attacks blocked by Microsoft Defender ATP
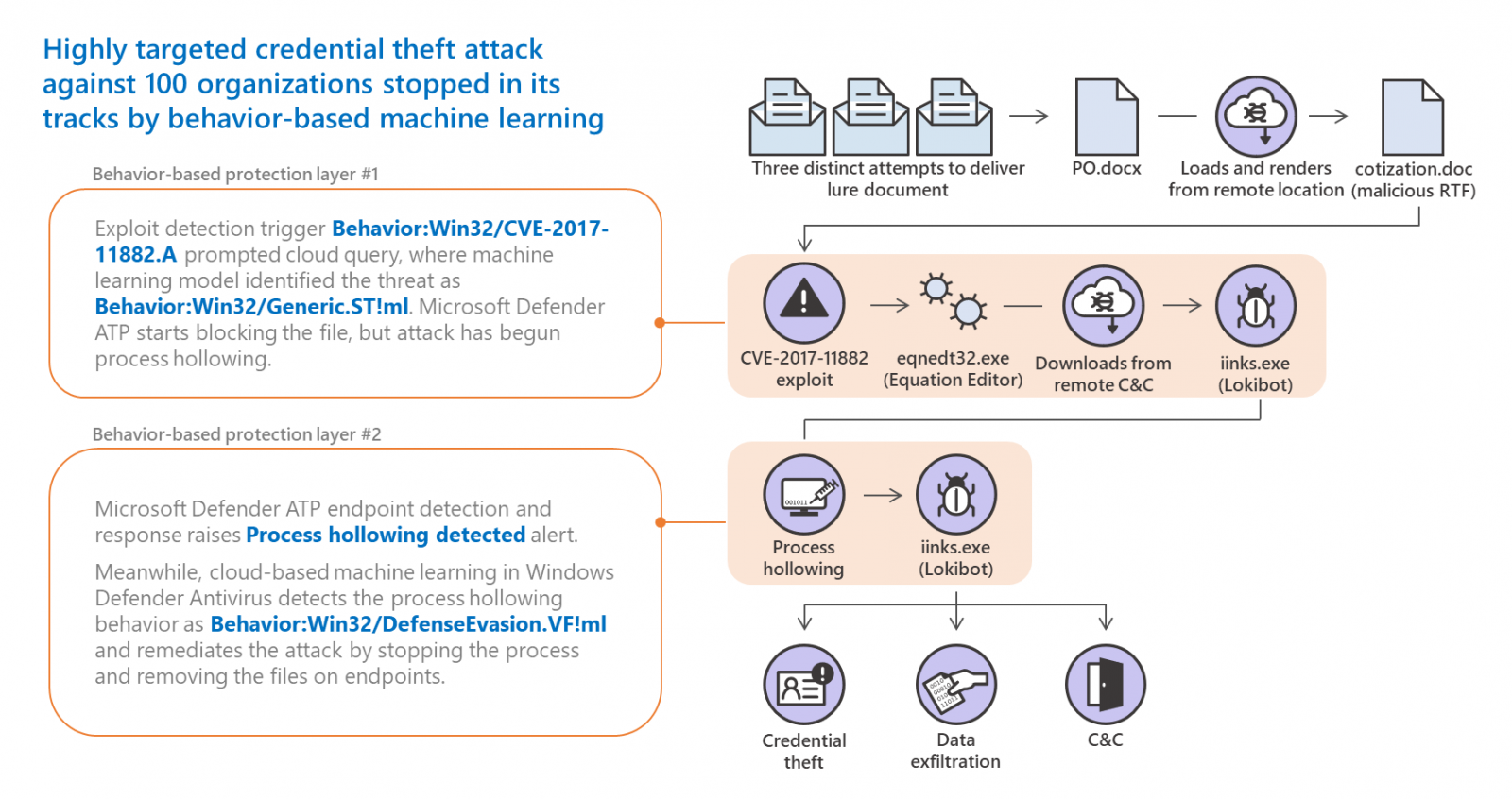
However, as Microsoft says, "the behavior-based machine learning models built into Microsoft Defender ATP caught attacker techniques at two points in the attack chain."
More exactly, it managed to detect the malicious attack's exploit behavior and the process hollowing technique used to inject malicious code into a running process after unmapping its memory.
Last month, Microsoft's researchers also spotted a new fileless malicious campaign, dubbed Nodersok by the Microsoft Defender ATP Research Team and Divergent by Cisco Talos, and observed it while dropping LOLBins to infect Windows systems using a Node.js-based malware that turned the devices into proxies.
During July, Microsoft discovered yet another fileless malware campaign dropping the information-stealer Astaroth Trojan into the memory of compromised computers.
Just like in the case of the Nodersok campaign detected in September, the attacks delivering Astaroth payloads used various fileless techniques and a multi-stage infection chain, with the initial vector being a spear-phishing email with malicious links.

Comments
Post a Comment