
Cybersecurity researchers at Check Point today disclosed details of two recently patched potentially dangerous vulnerabilities in Microsoft Azure services that, if exploited, could have allowed hackers to target several businesses that run their web and mobile apps on Azure.
Azure App Service is a fully-managed integrated service that enables users to create web and mobile apps for any platform or device, and easily integrate them with SaaS solutions, on-premises apps to automate business processes.
According to a report researchers shared with The Hacker News, the first security vulnerability (CVE-2019–1234) is a request spoofing issue that affected Azure Stack, a hybrid cloud computing software solution by Microsoft.
If exploited, the issue would have enabled a remote hacker to unauthorizedly access screenshots and sensitive information of any virtual machine running on Azure infrastructure — it doesn’t matter if they’re running on a shared, dedicated or isolated virtual machines.
According to researchers, this flaw is exploitable through Microsoft Azure Stack Portal, an interface where users can access clouds they have created using Azure Stack.
By leveraging an insure API, researchers found a way to get the virtual machine name and ID, hardware information like cores, total memory of targeted machines, and then used it with another unauthenticated HTTP request to grab screenshots, as shown.
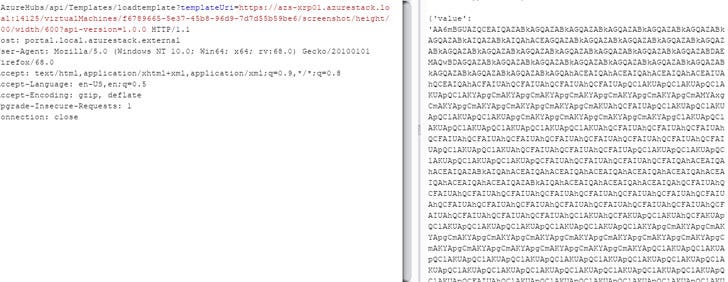
Whereas, the second issue (CVE-2019–1372) is a remote code execution flaw that affected the Azure App Service on Azure Stack, which would have enabled a hacker to take complete control over the entire Azure server and consequently take control over an enterprises’ business code.
What’s more interesting is that an attacker can exploit both issues by creating a free user account with Azure Cloud and running malicious functions on it or sending unauthenticated HTTP requests to the Azure Stack user portal.
Check Point published a detailed technical post on the second flaw, but in brief, it resided in the way DWASSVC, a service responsible for managing and running tenants’ apps and IIS worker processes, which actually run the tenant application, communicate with each other for defined tasks.
Since Azure Stack failed to check the length of a buffer before copying memory to it, an attacker could have exploited the issue by sending a specially crafted message to DWASSVC service, allowing it to execute malicious code on the server as the highest NT AUTHORITY/SYSTEM privilege.
“So how can an attacker send a message to DWASSVC (DWASInterop.dll)? By design, when running the C# Azure function, it runs in the context of the worker (w3wp.exe),” the researchers said.
“This lets an attacker the possibility to enumerate the currently opened handles. That way, he can find the already opened named pipe handle and send a specially crafted message.”
Check Point researcher Ronen Shustin, who discovered both vulnerabilities, responsibly reported the issues to Microsoft last year, preventing hackers from causing severe damage and chaos.
After patching both issues late last year, the company awarded Shustin with 40,000 USD under its Azure bug bounty program.
Check the original article: https://thehackernews.com/
Comments
Post a Comment